Security is one of those things that keeps DBAs awake at night, particularly if they are not following best practices and staying up to date with the latest security patches.
One key concept of security involves the principle of granting the “least privilege” to database users. This is done to avoid excessive privileges which can result in vulnerabilities, uncontrolled system access, and even data breaches.
One tool to combat such security concerns involves the use of a new feature available with Oracle 12c called Privilege Analysis. This option requires the Database Vault license in versions prior to 19c. With 19c, this tool now becomes a core component of Enterprise Edition.
Using this tool in combination with Oracle Enterprise Manager (OEM) provides a powerful mechanism for analyzing security permissions while easily identifying opportunities for improving the security posture across the enterprise. To implement Privilege Analysis through OEM, check out the below required steps to better ensure privileges will only be revoked if they are not being utilized.
Steps for capturing, generating, and reporting privilege usage
1. To capture the privilege usage of a given database, simply log on to OEM and select the target database. From the Database Home Page, select "Security/Privilege Analysis."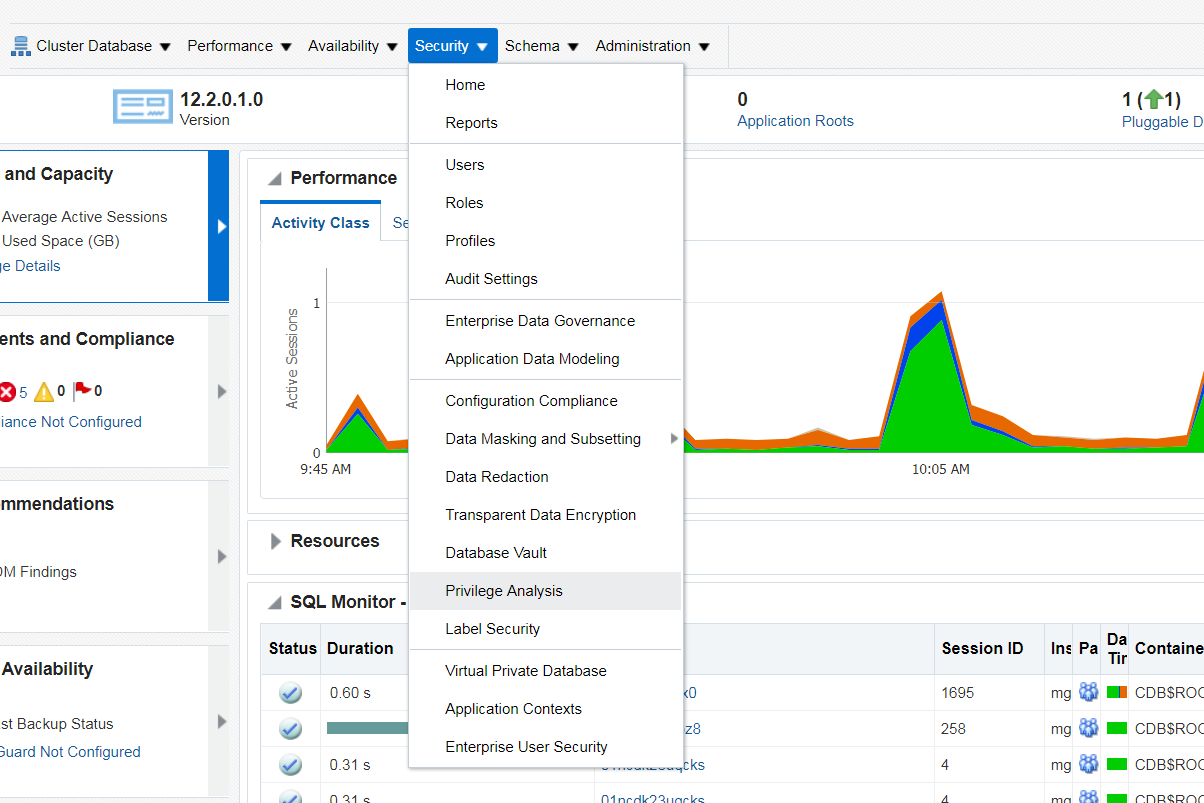
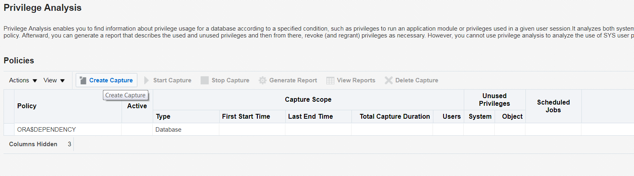
For the Policy Name, I would recommend using the database name with the start date appended on the end. This helps keep track of different captures you may have running and when the capture was initially setup.
For Scope, selecting “Database” provides an across-the-database view, allowing you to see all potential issues which would be considered important, particularly the first time this is run.

Please note: You will want to let the capture run for a lengthy period of time to ensure you are getting an adequate view of privilege usage by all database user accounts. As a general recommendation, a duration of several months seems appropriate but if you have special reports/processes that are run quarterly/semi-annually/annually then you may want to extend the run time longer in order to capture them.
5. The next step is to stop the capture. To do so, select the Policy and click on the “Stop Capture” button.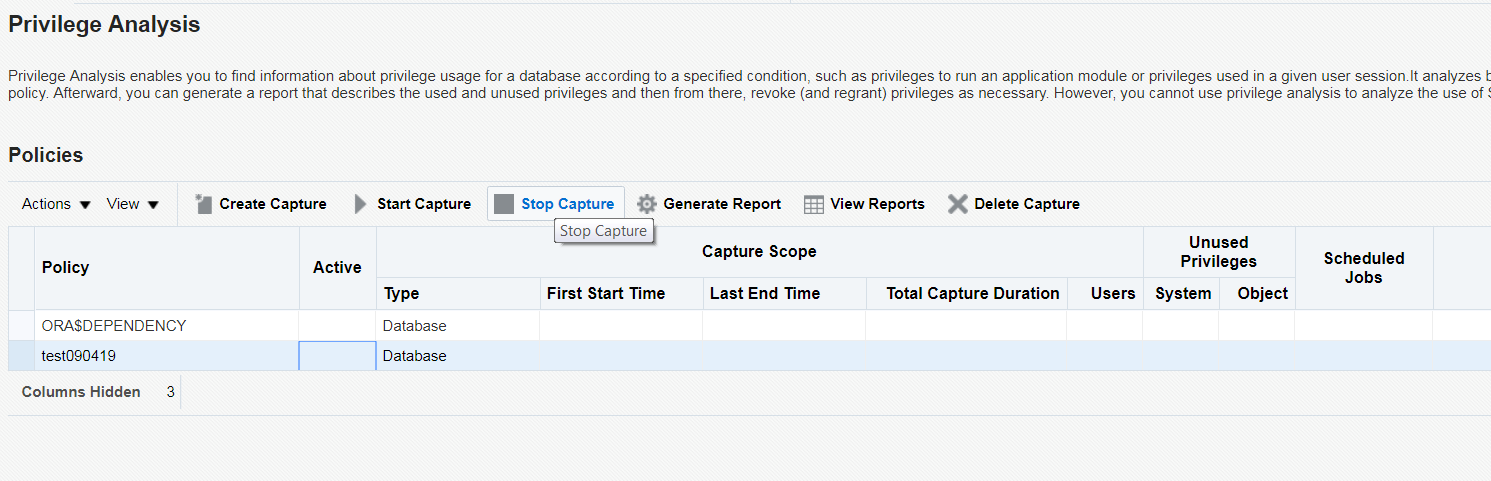


The below screen shows an example of a generated report.

You can drill down on any of the items in blue which will redirect you to a more detailed view. This allows you to pick and choose what you want to focus on when revoking unnecessary privileges. In addition, options are available for automatically revoking/regranting privileges through the GUI.
Final recommendations
Make changes in phases and devise a strategy to minimize the potential impact should things go south. Identifying the revokes which seem the most straightforward and least likely to cause catastrophic impact is a good way to maintain job security while making positive steps in the right direction toward implementing security best practices.
Having a test environment for testing changes is a must. If changes aren’t properly tested before deploying in production, you may find a line forming outside your cube or office wanting to know what’s wrong with the system shortly after making changes in production.
Have questions or comments? Get in touch with us any time. And if you are interested in learning some useful tips and tricks for your Oracle database upgrade, check out the first part of our blog series on this subject.















