Some customers want to change all passwords every 60 days, which is a more secure security practice yet is a burden to the administrative staff needing to work off hours due to the system impact.
Having recently attended an Oracle virtual conference, I was excited to learn Oracle 19c now has a backported Oracle 21c feature available as of 19.12 (July 2021 Quarterly patch). The feature allows for both the old and the newly changed passwords to be used at the same time for a duration specified by the DBA. The rolling password feature allows application servers to be restarted in a rolling fashion causing no outage to occur or account locks for application accounts.
Before walking through how to implement the rolling password feature, we need to address a few prerequisites:
- Configure your database with Oracle RAC (two-node minimum) to support rolling patching and maintenance.
- Implement Transparent Application Failover (TAF) so that queries/sessions will automatically switch from one node to another.
- Point all application connections to include database links to the TAF to minimize the impact of maintenance and unexpected outages.
- Utilize Data Guard with Oracle RAC or stand-alone databases for high availability.
Which configuration is right for your organization? It depends on costs, performance, and availability requirements while also considering skillset of those involved in maintaining the environments. In this case, one size does not fit all.
Now that you’ve implemented Oracle RAC with TAF, it’s time to make your applications ready for gradual password changes. This feature is controlled through an Oracle profile. Please note, if you are using multitenant or a container/pluggable database configuration, profiles are centrally managed in the container database. The first step should be to run the following script from your container database which will fix the DBA_PROFILES view to show the amount of time in days, not seconds.
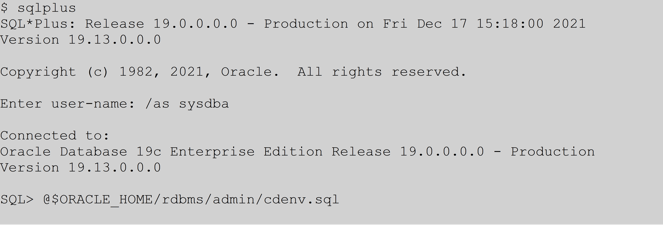
Next, to add this feature you would take an existing profile (let’s say app_connect_profile) and run the following command to change it to give you 10 days to make the application password change for a new password.
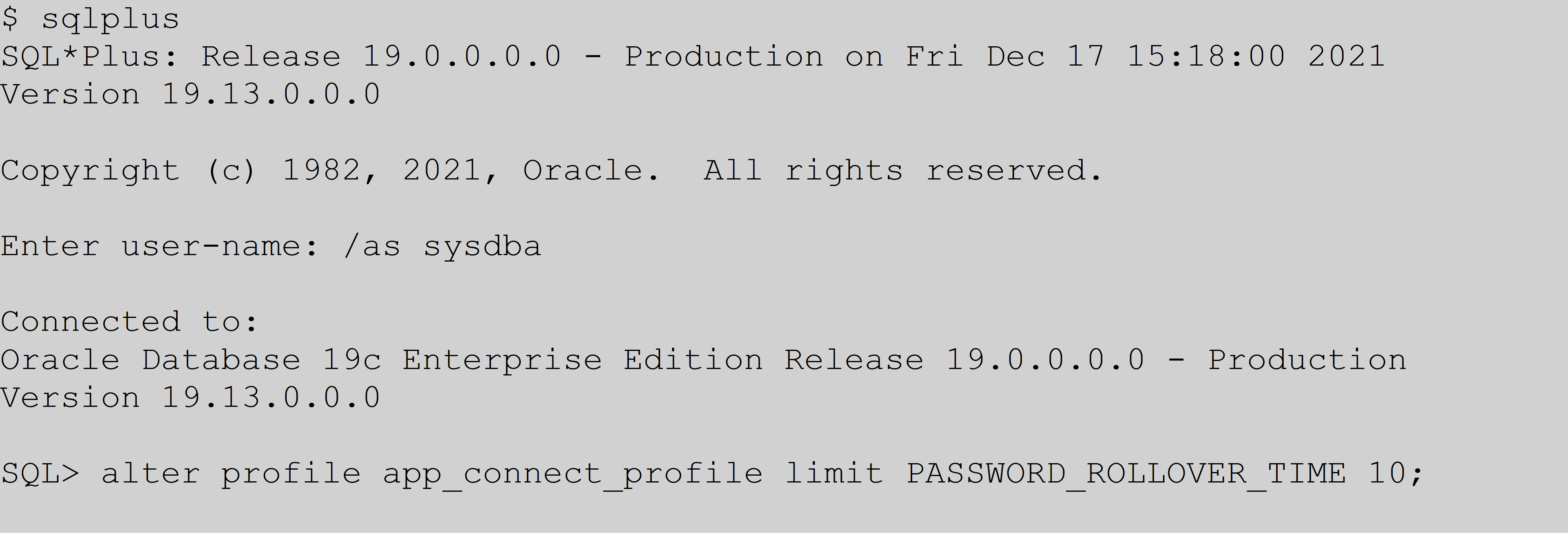
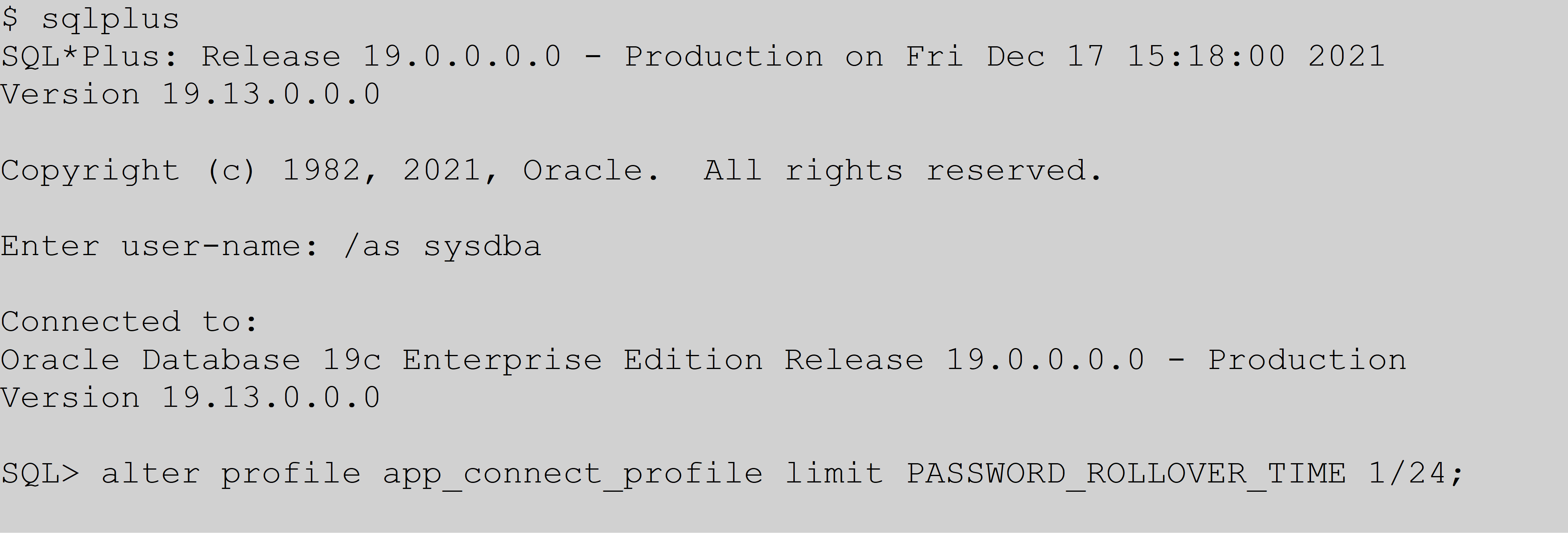
Based on the setting being in days, with a maximum of 60 days, you could theoretically take your sweet time in changing passwords. However, having two passwords that both work for this long could become a security threat. With this feature, Oracle gives you the flexibility to go the other extreme by allowing, in this example, one hour for application server password changes to be made with the below setting.
Please note, based on my experience, changing an existing profile did not by itself result in allowing both the old and new password to connect to the database for a user. Creating a new profile and setting the user to that profile didn’t work either. In both cases, I changed the password to a user, tried the old password and received ORA-1017 (invalid username/password). The new password connects with no issues, which it would do without this new feature so… not very helpful. It was like the new feature did nothing. After working with support to rule out a bug, a simple solution was provided. For each user, simply perform the following commands.

Is there something magical about the default profile? No, but changing from a profile and reassigning the original seems to address the issue. What’s interesting is that creating a new user and assigning them a profile with password_rollover_time set works with no issue. With existing users, you must either drop/recreate the user or follow the trick above.
Please note, altering the user profile as shown above is a onetime fix so a minor change for a long-term gain. Get your nights and weekends back with this great new feature by following this simple trick!
AEM can help your organization implement technologies such as Oracle Data Guard, Container/Pluggable Databases, and Oracle RAC with TAF configuration. Please reach out to learn more about our service offerings.















