... to replace the legacy Certification and Accreditation (C&A) process with a six-step lifecycle process used to obtain and maintain the Authority to Operate (ATO) federal systems. This new approach addresses risk-related concerns while providing a consistent, disciplined, and structured process integrating risk management activities into the system development life cycle (SDLC).
Introduction
RMF serves a federal mandate for agencies and organizations handling federal data and associated information. The conversion to RMF from the legacy process known as the Defense Information Assurance Certification and Accreditation Process (DIACAP) is the latest revision of the original C&A process scheduled to be completed by mid-2018.
RMF implementation is based on special publications from the National Institute of Standards and Technology (NIST) and the Committee on National Security Systems (CNSS). It focuses on selecting and implementing security and privacy controls to include ongoing continuous monitoring to assess the effectiveness of the controls.
Configuration Management (CM) requires these security controls be integrated from the beginning of the Software Development Life Cycle (SDLC) and continuously monitored for effectiveness (“baked-in”) versus adding the security controls after the system is in production (“bolted-on”).
RMF allows for Cybersecurity Reciprocity, which serves as the default for Assessment and Authorization of an IT System that presumes acceptance of existing test and assessment results. Cybersecurity Reciprocity provides a common set of trust levels adopted across the Intelligence Community (IC) and the Department of Defense (DoD) with the intent to improve efficiencies across the DoD Information Enterprise. Each component makes all cybersecurity authorization documentation available to other components via Enterprise Mission Assurance Support Service (eMASS). This eMASS tool provides a central location for managing all documentation, controls, and the like for working through the RMF process. The intent is to eliminate redundancy and unnecessary testing for streamlining all aspects of cyber security management.
Comparing RMF to DIACAP
Certification & Accreditation (C&A) versus Assessment & Authorization (A&A)
To clarify the process, the Certification & Accreditation process was changed to Assessment & Authorization. When systems are evaluated, they are not certified; instead, they are assessed. After the Designated Accrediting Authority (DAA) signs off for the system to go live or be allowed to remain operational, the system is authorized, not accredited.
The purpose of this approach was to avoid confusion as to what security a system needs. RMF eliminates the 3 year C&A cycle and replaces it with continuous ongoing monitoring and authorization with the concept that once an ATO has been awarded, security measures should be continuously evaluated for maintaining the overall security posture.
Interim Authority to Operate (IATO) Has Been Removed
Under the DIACAP C&A process, an IATO could be requested to allow for systems to be connected to the network for up to 180 days to allow for testing. A system could be allowed to have two consecutive IATOs. At the end of the IATO, systems must have security vulnerabilities remediated to obtain an Authorization to Operate (ATO). During this timeframe systems with security vulnerabilities are managed via a Plan of Actions and Milestones (POA&M).
RMF has replaced the IATO with an “ATO with conditions.” After the second ATO with conditions has ended, the authorization to operate must come from a higher tier.
Roles and Responsibilities Have Changed
Some roles and responsibilities along with terminology have changed with the transition to RMF. Some roles now include an Authorizing Official (AO), Security Control Assessor (SCA), Common Control Provider (CCP), Information Owner (IO), Information System Owner (ISO), Information System Security Manager (ISSM), Facility Security Officer (FSO), and Information System Security Officer (ISSO). This resource does a nice job of explaining these roles and associated responsibilities.
Categories and Classifications Levels
As part of this transition, RMF has replaced the DIACAP Mission Assurance Category (MAC) levels I, II, III with Impact Levels Low, Moderate, and High. RMF system categorization designates the Impact Level instead of MAC. In addition, RMF has replaced the DIACAP classification levels Classified, Sensitive, and Public with Security objectives Confidentiality, Integrity, and Availability. MAC designations and RMF impact levels do not correspond to each other.
RMF’s implementation is a more complex formula for assigning information assurance (IA) controls to systems. The categorization is not done by the mission the system performs, rather than by the information it protects.
The RMF Transition Process
In order to obtain an ATO, STIGs and Information System Controls are implemented along with creating mitigation plans for all open items. The ATO process leveraging the RMF should take around 8 months to complete, depending on a variety of factors. The below diagram depicts the process flow the Navy uses for the RMF, which should generically apply to all organizations.
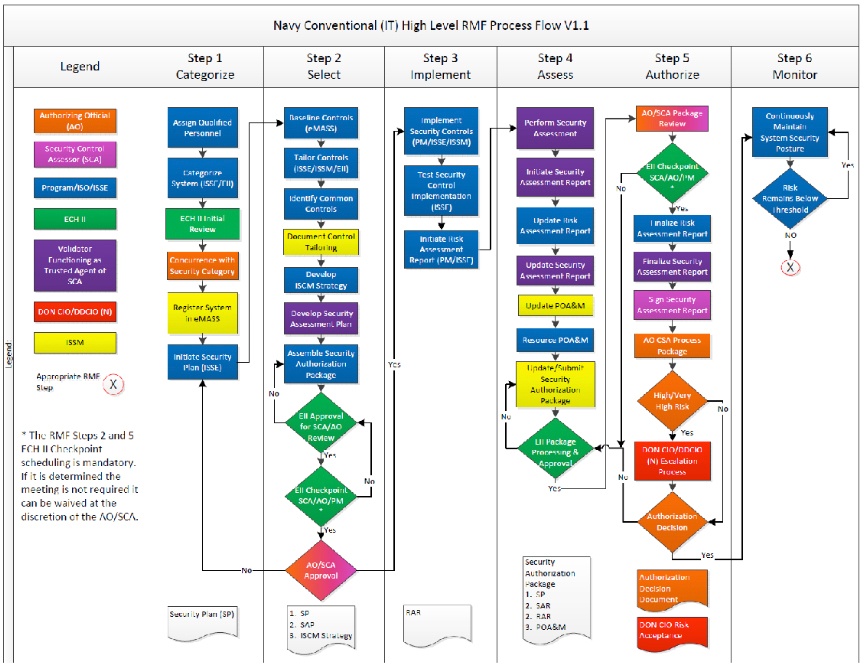
Transition Notes
There are many differences between RMF and DIACAP. Staff transition training is needed to lay the groundwork to achieve a successful RMF implementation. Transitioning to RMF represents a significant learning curve due to new processes and documentation required throughout. Not having sufficient documentation, lack of defined security practices, or having too many open findings are some examples of potential sources of delays.
Training will introduce cybersecurity staff to the new approach to protecting federal information assets, clarifying directives, and understanding the new nomenclature present throughout RMF. It is well-worth the investment for impacted personnel to attend RMF training to better understand the responsibilities, requirements, and methodology for successfully navigating this new frontier.
System categorization is the first step in the six steps to RMF implementation. Since the other steps depend on this being done correctly, it is important to identify all policies, procedures, and information types. All information that is processed, stored and transmitted on the system must be categorized using the new security objectives and impact levels.
If policies and procedures are not formally defined then time must be put into documenting these activities. All categorization steps will need be carefully documented to progress through the RMF process.
If Personally Identifiable Information (PII) is contained on the system, a Privacy Impact Assessment (PIA) must be completed and sent to the Department of the Navy Chief Information Officer (DONCIO) for Navy systems. Select the Privacy Overlay to add on to the baseline security controls when determining controls and overlays in step two.
You will need to consult eMASS and identify the automatically compliant Control Correlation Identifiers (CCI) that the DoD has defined as compliant by way of an existing policy or procedure (Cybersecurity Reciprocity).
You will need to verify the systems backup policy is reliable and is meeting all compliance requirements regarding encryption of stored data and destruction when discarding the media.
Finally, be sure to validate the testing plans for security controls to be implemented to ensure that it captures all components and scenarios. You’ll need to be able to provide the AO detailed documentation that explains the actions taken to implement controls and the intentions behind implementing them.
Hope this information is useful. If you are interested in learning more, this presentation provides a deeper dive into the RMF process.















